Salut,
voici le rapport de RogueKiller
RogueKiller V8.7.8 [Nov 14 2013] par Tigzy
mail : tigzyRKgmailcom
Remontees :
http://www.adlice.com/forum/
Site Web :
http://www.sur-la-toile.com/RogueKiller/
Blog :
http://tigzyrk.blogspot.com/
Systeme d'exploitation : Windows Vista (6.0.6002 Service Pack 2) 32 bits version
Demarrage : Mode normal
Utilisateur : Clemence [Droits d'admin]
Mode : Recherche -- Date : 11/14/2013 13:45:41
| ARK || FAK || MBR |
¤¤¤ Processus malicieux : 0 ¤¤¤
¤¤¤ Entrees de registre : 6 ¤¤¤
[HJ POL][PUM] HKCU\[...]\System : DisableTaskMgr (0) - TROUVÉ
[HJ SMENU][PUM] HKCU\[...]\Advanced : Start_ShowRecentDocs (0) - TROUVÉ
[HJ SMENU][PUM] HKCU\[...]\Advanced : Start_ShowPrinters (0) - TROUVÉ
[HJ SMENU][PUM] HKCU\[...]\Advanced : Start_ShowRun (0) - TROUVÉ
[HJ DESK][PUM] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) - TROUVÉ
[HJ DESK][PUM] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) - TROUVÉ
¤¤¤ Tâches planifiées : 0 ¤¤¤
¤¤¤ Entrées Startup : 0 ¤¤¤
¤¤¤ Navigateurs web : 0 ¤¤¤
¤¤¤ Fichiers / Dossiers particuliers: ¤¤¤
¤¤¤ Driver : [CHARGE] ¤¤¤
[Address] IRP[IRP_MJ_CREATE] : C:\Windows\system32\drivers\iastorv.sys - HOOKED (Unknown @ 0x862FD1F8)
[Address] IRP[IRP_MJ_CLOSE] : C:\Windows\system32\drivers\iastorv.sys - HOOKED (Unknown @ 0x862FD1F8)
[Address] IRP[IRP_MJ_DEVICE_CONTROL] : C:\Windows\system32\drivers\iastorv.sys - HOOKED (Unknown @ 0x862FD1F8)
[Address] IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : C:\Windows\system32\drivers\iastorv.sys - HOOKED (Unknown @ 0x862FD1F8)
[Address] IRP[IRP_MJ_POWER] : C:\Windows\system32\drivers\iastorv.sys - HOOKED (Unknown @ 0x862FD1F8)
[Address] IRP[IRP_MJ_SYSTEM_CONTROL] : C:\Windows\system32\drivers\iastorv.sys - HOOKED (Unknown @ 0x862FD1F8)
[Address] IRP[IRP_MJ_PNP] : C:\Windows\system32\drivers\iastorv.sys - HOOKED (Unknown @ 0x862FD1F8)
[Inline] EAT @explorer.exe (FwDoNothingOnObject) : FirewallAPI.dll - HOOKED (Unknown @ 0x3644FC66)
[Inline] EAT @explorer.exe (FwEnableMemTracing) : FirewallAPI.dll - HOOKED (Unknown @ 0x3644FC66)
[Inline] EAT @explorer.exe (FwSetMemLeakPolicy) : FirewallAPI.dll - HOOKED (Unknown @ 0x3644FC66)
[Inline] EAT @explorer.exe (?t@?1??get_instance@?$singleton@V?$oserializer@Vxml_woarchive@archive@boost@@VSessionIdContext@Common@@@detail@archive@boost@@@serialization@boost@@CAAAV?$oserializer@Vxml_woarchive@archive@boost@@VSessionIdContext@Common@@@detail@archive@4@XZ@4V?$singleton_wrapper@V?$oserializer@Vxml_woarchive@archive@boost@@VSessionIdContext@Common@@@detail@archive@boost@@@634@A) : ContextMenuExt.dll - HOOKED (C:\Windows\system32\SYNCENG.dll @ 0x67564853)
¤¤¤ Ruches Externes: ¤¤¤
¤¤¤ Infection : ¤¤¤
¤¤¤ Fichier HOSTS: ¤¤¤
-- %SystemRoot%\System32\drivers\etc\hosts
127.0.0.1 localhost
::1 localhost
¤¤¤ MBR Verif: ¤¤¤
+++++ PhysicalDrive0: (\\.\PHYSICALDRIVE0 @ IDE) Hitachi HTS543225L9A300 ATA Device +++++
--- User ---
[MBR] 855cb12788d916f54065960cb9113f6a
[BSP] 18ab90659ef6c65dd8e94aaa6e29c7de : MBR Code unknown
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 63 | Size: 228960 Mo
1 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 468912128 | Size: 9511 Mo
User = LL1 ... OK!
User = LL2 ... OK!
+++++ PhysicalDrive1: (\\.\PHYSICALDRIVE1 @ USB) WD My Passport 0748 USB Device +++++
--- User ---
[MBR] 80437cd8b9e3133868a6b0722d39af1b
[BSP] 9b6ebbf7c1a08cbb9ccbeeaea6641cdb : Windows XP MBR Code
Partition table:
0 - [XXXXXX] NTFS (0x07) [VISIBLE] Offset (sectors): 2048 | Size: 476907 Mo
User = LL1 ... OK!
Error reading LL2 MBR!
Termine :
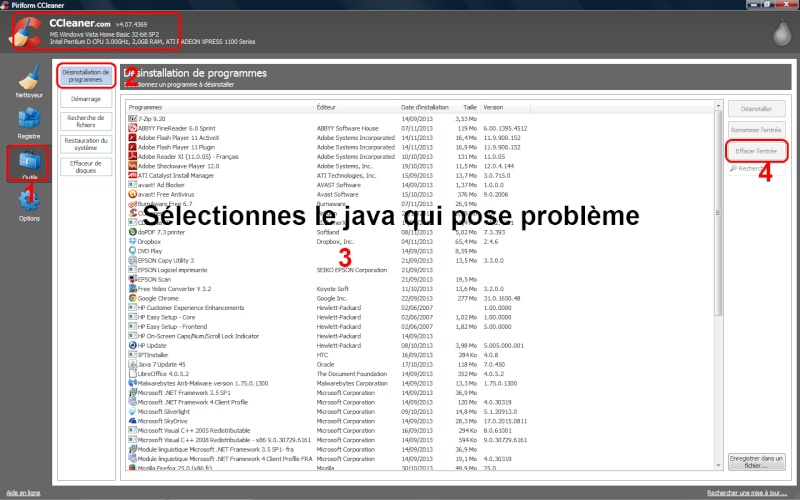
Pour java voila ce que l'outil me dit quand je suis la procédure indiquée ci-dessus :
[img]
[img]http://i56.servimg.com/u/f56/11/59/36/41/pc610.png[/img][/img]