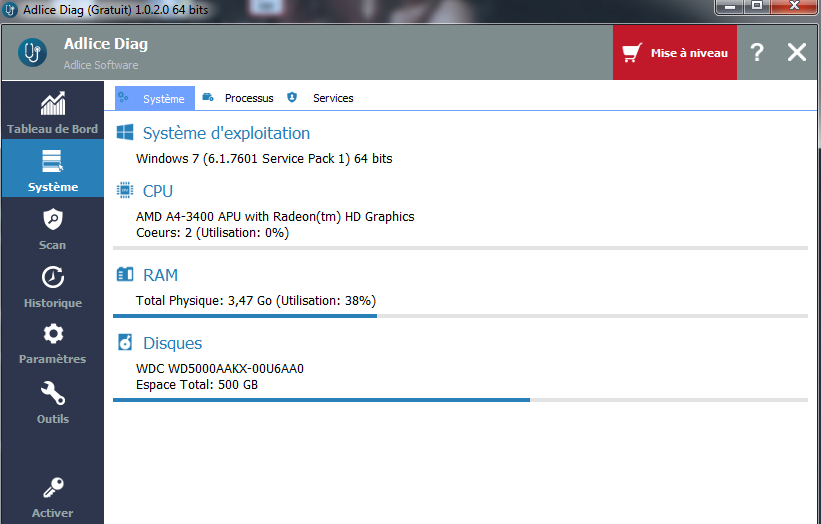
Hello DID
C est bizarre : ça fait plusieurs fois que je te réponds et mon message semble disparaitre du forum.
Ci joint le rapport Maleware d'hier :
Malwarebytes
www.malwarebytes.com
-Détails du journal-
Date de l'événement de protection: 03/03/2020
Heure de l'événement de protection: 09:00
Fichier journal: 05bdc46f-5d25-11ea-b358-54e1ad8f8b72.json
-Informations du logiciel-
Version: 4.0.4.49
Version de composants: 1.0.823
Version de pack de mise à jour: 1.0.20150
Licence: Premium
-Informations système-
Système d'exploitation: Windows 10 (Build 18362.657)
Processeur: x64
Système de fichiers: NTFS
Utilisateur: System
-Détails du site Web bloqué-
Site Web malveillant: 1
, C:\Users\edema\AppData\Roaming\Cosekasonab.exe, Bloqué, -1, -1, 0.0.0
-Données du site Web-
Catégorie: Cheval de Troie
Domaine: d1pobxbdnb8vsp.cloudfront.net
Adresse IP: 13.225.29.156
Port: 80
Type: En sortie
Fichier: C:\Users\edema\AppData\Roaming\Cosekasonab.exe
(end)
Egalement le rapport de ce matin :
Malwarebytes
www.malwarebytes.com
-Détails du journal-
Date de l'analyse: 04/03/2020
Heure de l'analyse: 02:02
Fichier journal: c72e6264-5db3-11ea-a9b4-54e1ad8f8b72.json
-Informations du logiciel-
Version: 4.0.4.49
Version de composants: 1.0.823
Version de pack de mise à jour: 1.0.20182
Licence: Premium
-Informations système-
Système d'exploitation: Windows 10 (Build 18362.657)
Processeur: x64
Système de fichiers: NTFS
Utilisateur: System
-Résumé de l'analyse-
Type d'analyse: Analyse des menaces
Analyse lancée par: Planificateur
Résultat: Terminé
Objets analysés: 334460
Menaces détectées: 21
Menaces mises en quarantaine: 0
Temps écoulé: 7 min, 37 s
-Options d'analyse-
Mémoire: Activé
Démarrage: Activé
Système de fichiers: Activé
Archives: Activé
Rootkits: Désactivé
Heuristique: Activé
PUP: Détection
PUM: Détection
-Détails de l'analyse-
Processus: 0
(Aucun élément malveillant détecté)
Module: 0
(Aucun élément malveillant détecté)
Clé du registre: 1
PUP.Optional.WinYahoo.TskLnk, HKLM\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\UNINSTALL\{14E9FC29-4469-2DA9-F5E9-5D2925698EA9}, Aucune action de l'utilisateur, 871, 542290, , , ,
Valeur du registre: 0
(Aucun élément malveillant détecté)
Données du registre: 0
(Aucun élément malveillant détecté)
Flux de données: 0
(Aucun élément malveillant détecté)
Dossier: 2
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\USERS\EDEMA\APPDATA\LOCAL\{150F2353-31A7-4FEB-5C3F-6A037857969B}, Aucune action de l'utilisateur, 871, 542290, 1.0.20182, , ame,
Fichier: 18
PUP.Optional.WinYahoo.TskLnk, C:\USERS\EDEMA\APPDATA\ROAMING\Microsoft\Windows\Start Menu\Programs\HowToRemove.lnk, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\USERS\EDEMA\APPDATA\LOCAL\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HOWTOREMOVE\HOWTOREMOVE.HTML, Aucune action de l'utilisateur, 871, 542290, 1.0.20182, , ame,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\chromium-min.jpg, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\control panel-min-min.JPG, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\down.png, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\ff menu.JPG, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\ff search engine-min.png, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\hp-min ff.png, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\hp-min ie.png, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\search engine.gif, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\setup pages.gif, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\sp-min.png, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\start-min.jpg, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\HowToRemove\up.png, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\fenedo, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\fodeco, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\uninst.exe, Aucune action de l'utilisateur, 871, 542290, , , ,
PUP.Optional.WinYahoo.TskLnk, C:\Users\edema\AppData\Local\{150F2353-31A7-4FEB-5C3F-6A037857969B}\uninstp.dat, Aucune action de l'utilisateur, 871, 542290, , , ,
Secteur physique: 0
(Aucun élément malveillant détecté)
WMI: 0
(Aucun élément malveillant détecté)
(end)
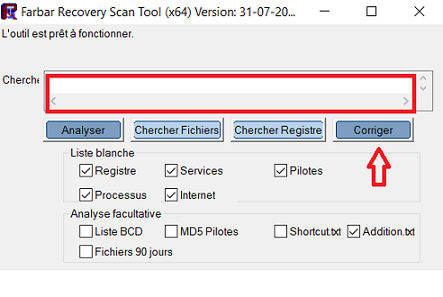

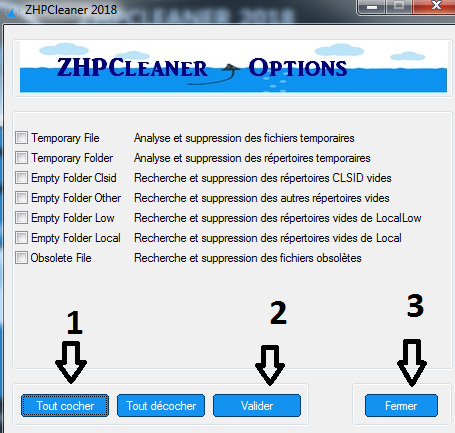

 AdliceDiag
AdliceDiag